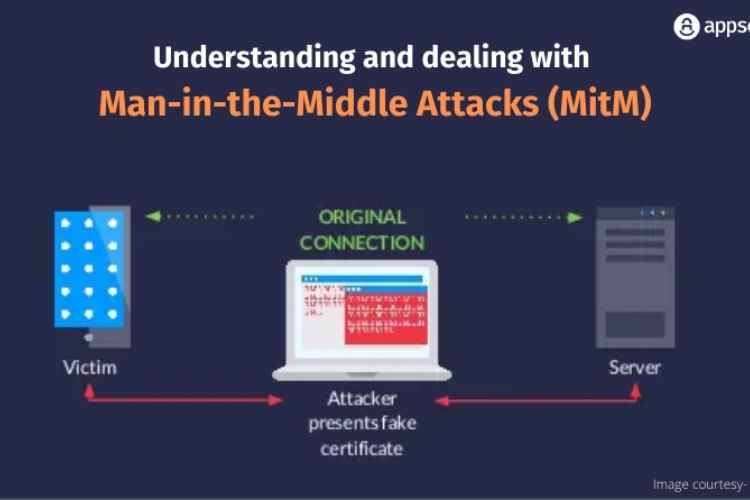
There are different cyber-attacks that are becoming a big threat for everyone. Of course, if you are not careful enough, you could be the next victim of these attacks. One important attack that you should definitely know about is a man-in-the-middle (MitM) type of attack. It is a type of cyberattack where important information is interrupted by an attacker making use of a method to interject themselves into the communication procedure.
The attacker here can be a passive type of listener in your conversation, he might be silently stealing your secrets, or he can even be an active participant, changing the contents of your messages. He can even be imitating the person or that of system you think you are speaking with. So, it is all about MiTM attack in simple words. Just think about your childhood when your sibling used to take the call on your behalf, mimic your voice and attitude and talk to the other person. It is just like that.
Working of a Man-in-the-Middle Attack
Well, most of the MitM type of attacks follow a straightforward type of order of operations. It is irrespective of the particular method used in the attack. Here in this example, there are three entities, Miley, Bob, and Jim (the attacker).
1. Jim secretly listens to a channel where Miley and Bob are communicating
2. Miley sends a text to Bob
3. Jim interrupts and reads Miley’s message without Miley or Bob having any idea about it.
4. Jim alters messages between Miley and Bob, triggering unwelcome or damaging responses.
Well, MitM methods are usually employed early in the cyber kill chain, it is during reconnaissance, intrusion, and even that of exploitation. Attackers or criminals most of the times use MitM to yield credentials and accumulate intelligence about their targets.
Remember that multi-factor authentication (MFA) may become an effective and efficient safeguard against any type of stolen credentials. Even if your username as well as password got scooped up by a man-in-the-middle, they would actually require your second factor to make proper use of them. However, it is quite unfortunate that in some cases, it is possible to bypass MFA.
Now, for your better understanding, here is a practical instance of a real-world MiTM type of attack against Microsoft Office 365 wherein MFA got bypassed by the attacker:
1. a user taps on a phishing link that carries them to a fake Microsoft sign page where they step in their username as well as password
2. The fake site page simply forwards the username as well as password to the server of the attacker
3. The attacker simply forwards the sign in request to Microsoft, so they do not simply raise any doubt
4. Microsoft simply sends the two-factor authentication code to the specific user through SMS
5. User puts the code into the false webpage
6. The false page forwards 2FA code to the server of the attacker
7. The attacker makes use of Evilginx to snip the session cookie
8. The attacker simply forwards the 2FA code of the user to Microsoft, and now the attacker is in the position to sign in to Office 365 as the compromised user by making use of the session cookie, and has proper access to sensitive data within the enterprise.
The Techniques and types of MitM type of Attack
There are different techniques that attackers use for this attack. And a few of such techniques are as under:
DNS Cache Poisoning
DNS cache poisoning is once the attacker gives you a false DNS entry that heads to a dissimilar website. It could look like Google, but it is not really Google, and the attacker takes away or captures whatever data like that of username and password that you enter into the false website.
1. Jim finds out that you use a specific type of DNS resolver.
2. Jim knows such a resolver is susceptible to exploits, such as an older version of that of BIND.
3. Jim makes use of this exploit to inform the DNS resolver that www.instance.com lives at a specific IP address that they own.
4. You visit www.instance.com from your computer, and then the DNS resolver informs you that the IP address of that specific website is the machine o the attacker!
5. Jim finishes the connection to the real website so you don’t really realize there is anybody hearing to all this, but he is in a position to able to see all the packets that you (or anybody else that uses this DNS resolver to link to www.instance.com) are actually sending.
ARP Cache Poisoning
Address Resolution Protocol (ARP) is a type of low-level process that simply translates the machine address (MAC) to that of the IP address on the local network. Here the criminal or attackers inject wrong information into this system to hoax your computer to think the attacker’s computer is the type of network gateway. Once you connect to the network, the attacker gets all of your network traffic (rather than your real network gateway) and simply passes the traffic along to its real place. You think that everything is normal. The attacker is in a position to witness all of your packets.
1. Jim (the attacker) joins your network and then runs a specific network sniffer
2. Jim reviews your network packets to try to predict the sequence numbers of your packets between the gateway and you
3. Jim then sends a packet to your computer with the wrong or false source address of the gateway and the right ARP sequence to dupe your computer into thinking the computer of the attacker is the gateway
4. Simultaneously, Jim floods the gateway with that of a Denial of Service (DoS) type of attack so you get the fake ARP packet before the gateway is in a position to respond
5. Jim misled your computer into rational the attacker’s laptop is the real type of gateway, and the MitM attack becomes successful
Conclusion
So, you now have a good understanding of man in the middle attack or that of MiTM type of attack. Make sure that you are vigilant about everything. You can look for some secure solutions from Appsealing to ensure that your platform is safe.